Banking Scam Security: GozNym Malware Steals Millions
Eastern European Cyber Crooks Raid US Banks For $4 Million In Just 3 Days A new banking trojan named GozNym is actively hitting U.S. and Canadian banks and has already taken about $4 million from two dozen North American banks.
IBM’s X-Power Research group reported that 24 banks in the two nations, 22 in the U.S., have so far lost about $4 million to assaults utilizing GozNym since the malware was found not long ago. Who directed the assaults is not known.
Limor Kessem, official security advisor for IBM, wrote in a web journal that GozNym was made by consolidating a percentage of the source code from the more seasoned Nymaim and Gozi IFSB saving money malware to make a much more perilous bit of programming. “From the Nymaim malware, it influences the dropper’s stealth and determination; the Gozi ISFB parts add the keeping money Trojan’s abilities to encourage misrepresentation by means of tainted Web programs,” said Kessem. “The final result is another managing an account Trojan in nature.”
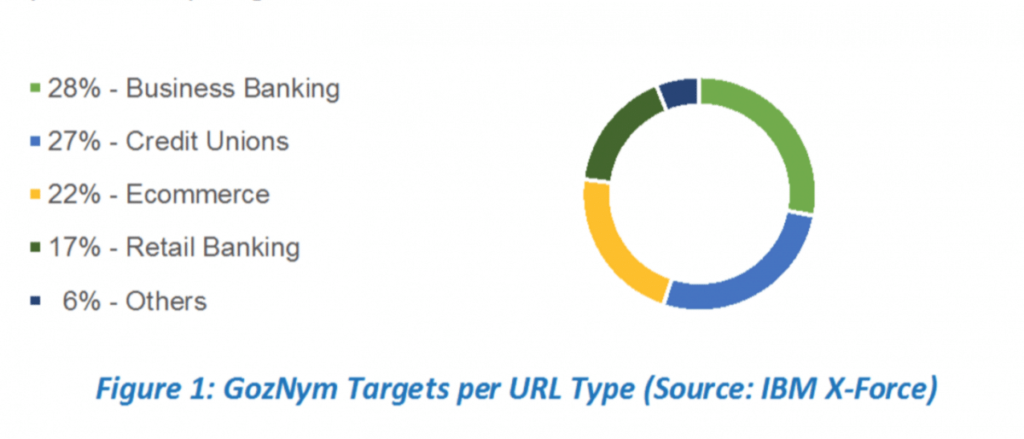
Assaults are so far pretty uniformly part with business banks engrossing 28 percent of the assaults; credit unions, 27 percent; e-trade 22 percent; retail managing an account, 17 percent; and the staying six percent were in different sorts of foundations. GozNym utilizes its local Nymaim capacity to penetrate its objectives through an endeavor pack which drops a payload into the framework that utilizations two executables for the disease schedule, IBM said.
Giovanni Vigna, fellow benefactor and boss innovation officer of Lastline, told in an email Thursday that malware like GozNym is not out of the ordinary at this point. “While it is intriguing to see two strands of malware turning out to be nearly entwined, it is not astonishing. With respect to any product that must be adaptable and dependable, malware has been modularized for some time, so usefulness can be reused or stacked as-required.
One industry official said it was baffling that GozNym has been effective in light of the fact that, while this malware is new, the kind of assault has been seen before and the saving money industry was advised to be careful.
“When you see an assault like GozNym getting bits of past malware to swipe another $4 million, it stings in case you’re a security proficient. You know you told both IT and the business how they expected to respond to assaults of this write when the first dangers rose. This fair demonstrates to you that they didn’t generally listen then,” Jonathan Sander, VP at Lieberman Programming, told in an email Thursday. Sanders portrayed this absence of worry as like that of a home that continually torn into through an open window in light of the fact that the proprietor declines to recall to bolt it.